
Top stories






More news

Marketing & Media
Ads are coming to AI. Does that really have to be such a bad thing?















REvil hackers reportedly exploited multiple previously unknown vulnerabilities in IT management software made by Kaseya. The Dutch Institute for Vulnerability Disclosure worked with Kaseya to fix the security flaws in its Virtual System Administrator software when the attack occurred, but the hackers were still able to capitalise on the vulnerabilities.
The biggest business that has acknowledged being impacted by the attack is the Swedish supermarket chain Coop, according to MyBroadband. Coop could not open over 800 stores because the attack affected its payment systems.
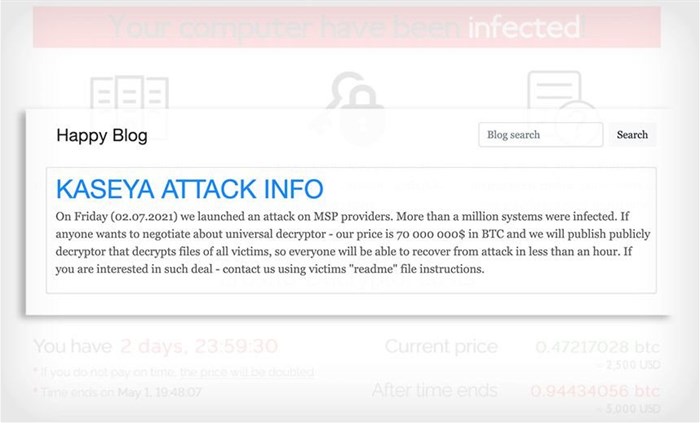
Based on IT security company Sophos threat intelligence, REvil has been active in recent weeks, including in the JBS attack, and is currently the dominant ransomware gang involved in Sophos’ defensive managed threat response cases.
Ross McKerchar, Sophos vice president and chief information security officer, said:
"This is one of the farthest-reaching criminal ransomware attacks that Sophos has ever seen. At this time, our evidence shows that more than 70 managed service providers were impacted, resulting in more than 350 further impacted organisations. We expect the full scope of victim organisations to be higher than what’s being reported by any individual security company. Victims span a range of worldwide locations with most in the United States, Germany and Canada, and others in Australia, the UK and other regions."
Mark Loman, Sophos director of engineering, said:
“Sophos is actively investigating the attack on Kaseya, which we see as a supply chain distribution attack. The adversaries are using MSPs as their distribution method to hit as many businesses as possible, regardless of size or industry type. This is a pattern we’re starting to see as attackers are constantly changing their methods for maximum impact, whether for financial reward, stealing data credentials and other proprietary information that they could later leverage, and more."
“A day after the attack, it became more evident that an affiliate of the REvil Ransomware-as-a-Service (RaaS) leveraged a zero-day exploit that allowed it to distribute the ransomware via Kaseya’s Virtual Systems Administrator (VSA) software. Usually, this software offers a highly trusted communication channel that allows MSPs unlimited privileged access to help many businesses with their IT environments," said Loman.