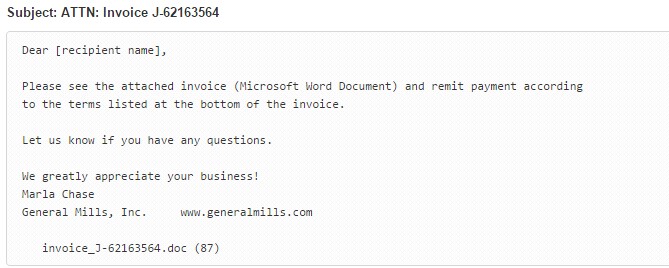
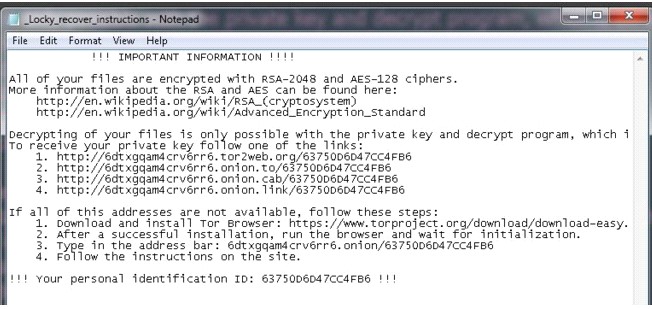
A new strain of ransomware has come to the fore. The strain has been dubbed Locky because of the way it renames the file extension.
Locky targets users via email attachments, which is often an invoice in a Microsoft Word document. Once the recipient downloads the file, if Office macros are enabled, the malicious macro gets to work encrypting the user's files. If macros are not enabled, the Word document will display a message prompting the user to enable macros in order to read the invoice.
What makes Locky so disastrous is that it is able to encrypt most file formats and encrypts all files it can access replacing the content with .locky extension. The victim is then prompted via a file called “_locky_recover_instructions.txt” to pay the ransom. Ransom demands range between 0.5 Bitcoin to 2 Bitcoin which is equivalent to around R3,336 – R 13,341.
Jeremy Matthews, country manager for Panda Security says, “The first Locky ransomware attacks targeted approximately 400,000 victims globally with infections continuing to rise”, Matthews continues, “South African stats are not clear yet, however, Panda Security has in the last week been approached by a number of local organisations looking for more effective security solutions after having been hit by Locky.
In light of this new threat, what can you do to keep your network safe? Basic preventative measures include:
• Do not open unsolicited email attachments
• Backup your data off site
• Do not enable Macros
However, these traditional approaches and conventional AV are no longer enough to protect users against cybercriminals who are constantly creating new ransomware. At Panda Security we have recognised the need to develop security solutions that address a changing cyber threat landscape.